Then yes, you’d probably be fine with any competent minipc and your favorite flavor of firewall… I would recommend OPNSense personally, but there’s others out there that I’m sure would meet your needs.
Just about any decent minipc can handle 1gbps from what I’ve seen a few years ago. You need much bigger horses to get up to 10gbps. But wouldn’t know what the minimum specs would be… I’ve been stuck in the higher end world for a while… So that information has kind of vanished from my memory… Someone else can chime in? I suspect the little baby n150 units could probably do 1gbps. Especially since you’re only doing minimal throughput on your wireguard as well (I have a few nodes and can push into 1gbps, so once again I’m resource heavy… and thus don’t have the lower requirements committed to memory anymore).
ISP -> ARRIS modem -> minipc -> Switch -> anything else you need including access points.
All of the “routers” that have wifi and a boatload of ports (unless we’re talking enterprise stuff) are all hybrid devices that are router+switch+AP, this is convenient for typical consumers, but quite restrictive for those who want to go prosumer or higher. For example… Wifi 7 just released last year. I swapped my AP out and now I have it. I can also mount that AP into the ceiling where it will give me the best coverage. Rather than the consumer answers of “replace the whole unit” or “add a shitton of mesh nodes that ultimately kind of suck” solutions that manufacturers love cause you spend more money on their products. Or other answers like you want to add a PoE device… well now that consumer unit is useless to you.




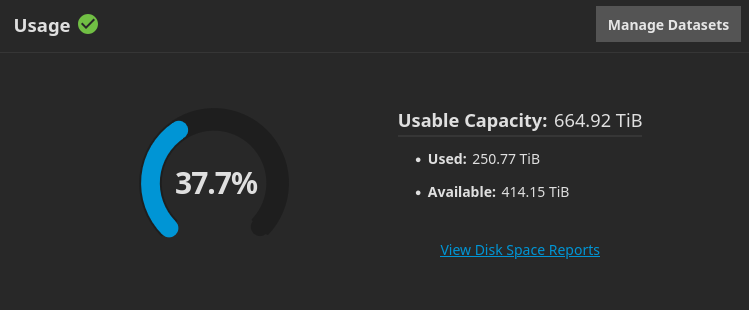
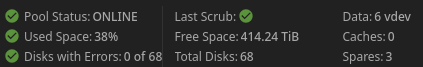
I’ve shared it on lemmy before somewhere…
Yeah found it… This thread. https://lemmy.saik0.com/post/1588364
For the stuff I do… it’s not overkill at all. By a metric of any individual’s house… yeah… it’s pretty overkill.